Abstract
Purpose of This Document
The goal of this document is to provide a succinct summary of various identity-related technologies developed in and around W3C that increase the capabilities of Media applications on the Web, and how they apply more specifically in a broadcasting-industry context.
Target Audience
This note is aimed at those who are unfamiliar with current identity technologies on the Web. Specifically, this note has been authored with broadcasters, ad agencies, non-web developers and end-users in mind. We hope that after reading this note readers will have a better understanding of identity technologies and that they will be better prepared to consider business and/or service models using these technologies with broadcasting.
1. Identity Technologies
1.1 OpenID

OpenID
- Characteristics
- OpenID is an open standard for authentication.
- OpenID is a decentralized Single Sign On system for the Web.
- OpenID is a URI, e.g. http://yosukef.myopenid.com/
- Basic Information
- SDO: OpenID Foundation [site]
- Creation Date: Summer, 2005
- Adoption: Over one billion OpenID-enabled user accounts and over 50,000 websites accepting OpenID for logins [page]
- License: Non-exclusive, royalty free, worldwide copyright license [pdf]
- Specs: OpenID Authentication 2.0
- Primary Functions
- Authentication
- SSO
- Ownable and movable identity
- Profile management
- Simplified registration process on each OpenID-enabled web site.
- Important Actors
- End-user
- OpenID Provider (OP)
- OP stores and authenticates End-user's credentials and profiles, and is responsible for securing them and providing them to other web services.
- Relying Party (RP)
- RP is any web service that relies on OP(s) for End-user authentication.
- Primary Scenarios
- End-user creates his or her OpenID at an OP's web site.
- RP maintains a list of OPs that the RP relies on.
- OP authenticates End-user with OpenID. RP doesn't.
- End-user can login to any RP web site using his or her OpenID with the help of an OP.
- End-user can't login to RP web sites if the RPs don't rely on the OP that the End-user has designated.
- End-user can change OP and maintain his or her OpenID if they provided a URI at the time they created the OpenID.
- End-user can simplify common profile information and store it centrally.
- Note
- Anybody can become an OP without the need for permission or a license from any party.
- Further Reading
1.2 WebID

WebID
- Characteristics
- WebID is an open standard for authentication.
- WebID is a Hash URI, e.g. http://www.w3.org/People/Berners-Lee/card#i that points to a person's WebID Profile document, a type of web page that must be available in Turtle format, but may also be available in other RDF serialisation formats from the same URLs.
- A Hash URI contains a fragment, a special part that is separated from the rest of the URI by a hash symbol (“#”).
- The WebID protocol is an authentication protocol on the Web. It enables people to authenticate onto WebID-enabled sites by selecting one of the certificates installed in their keychain through a web browser. CAs and anybody using X.509 tools can create these certificates.
- Basic Information
- Primary Functions
- Authentication
- SSO
- Ownable and movable identity
- Independently issued X.509 certificates as credentials
- Non-hierarchical approach and web of trust
- Profile management
- Fully integrated profiles
- FOAF ontology
- Important Actors
- Alice
- Alice is an agent who owns a Server which runs a service which Bob wishes to access
- Bob
- Bob is an agent who uses a Client to connect to Alice's service
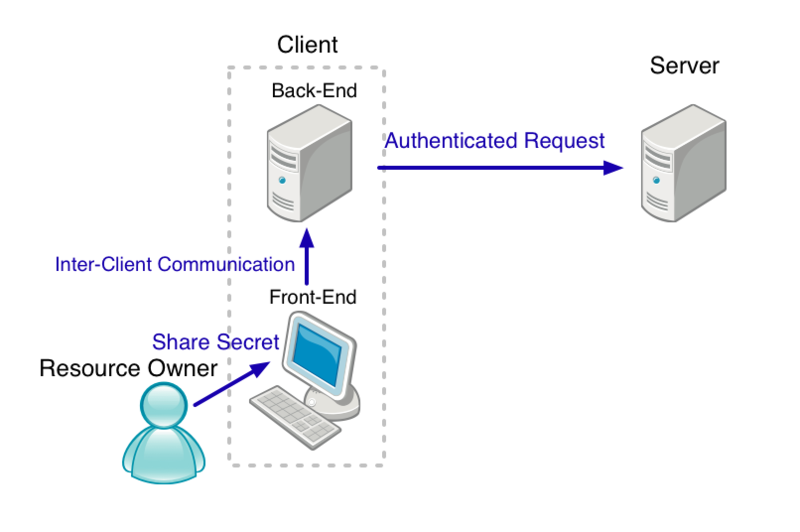
- Client
- The Client initiates a request to a service listening on a specific port using a given protocol on a given Server. It can request authentication credentials from a keychain to send to a server
- In the scenarios below, "Client" means a web browser.
- Server
- A Server is a machine contactable at a domain name or IP address that hosts a number of globally accessible services.
- In the scenarios below, "Server" means a web server.
- WebID Profile Service
- A web service that creates, stores and publishes WebID Profile documents.
- WebID Certificate Issuer
- An entity that issues X.509 certificates specified in the WebID standard such as CAs and engineers who use X.509 tools.
- Primary Scenarios
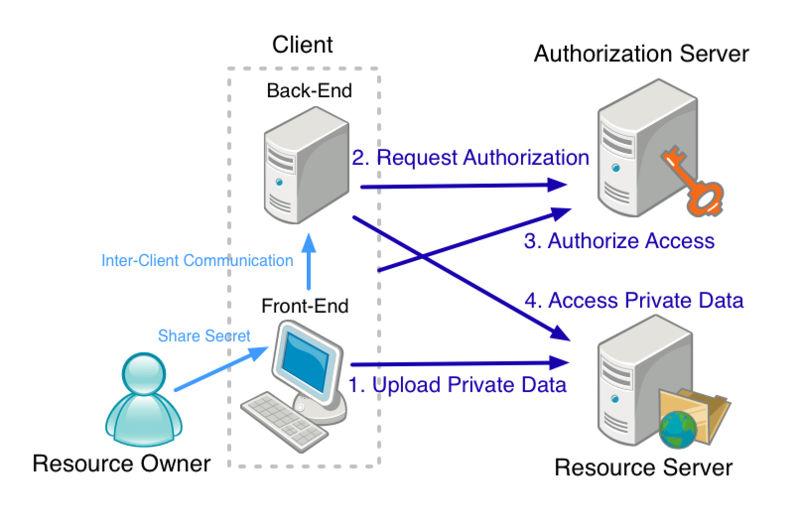
- Create a WebID Profile document at a WebID Profile Service
- Bob accesses a WebID Profile Service and enters private information he wants to publicly share, then he defines his hash fragment included in the WebID URL.
- The WebID Profile Service creates and stores Bob's profile document containing his private information. The URL of the profile document is his WebID and is now published and publicly accessible.
- Create a certificate bound to the WebID or WebID Profile document
- Bob provides his WebID to a WebID Certificate Issuer.
- WebID certificates are based on public key encryption technology and are in X.509 format. Certificates contain public key information and keychains in the end-user's environments store private keys.
- Incidentally, Bob could issue his own certificate if he had the skills and tools to create a certificate.
- The WebID Certificate Issuer returns a certificate tied to his WebID which is then stored in the keychain of Bob's Client.
- Bob provides the WebID Profile Service with the public key in the certificate. The WebID Profile Service publishes the public key as a part of his WebID document.
- Sign on a WebID-enabled site with the WebID
- Bob accesses Alice's Server that provides web services and requires authentication. The Server is WebID-enabled.
- Bob selects the WebID sign-on option in a pop-up window shown by the Client.
- Bob's Client shows a list of certificates in its keychain.
- Bob selects a certificate bound to his WebID and the Client sends the certificate and a token signed by his private key to the Server.
- The Server verifies Bob's identity in two steps:
- Step 1: Verify that Bob owns the certificate
- Receive the certificate and token
- Verify that the token was signed by the private key paired to the public key in the certificate
- Step 2: Verify this same Bob also owns the WebID Profile document
- Retrieve the profile document from the WebID or a Hash URI contained in the certificate
- Extract a public key (a modulus and public exponent) from the profile document
- Verify that the public key is identical to those in the certificate
- If verification succeeds, the Server allows the Client to access its services.
- Note
- Authorization by FOAF and WebID
- As described in FOAF section below, the combination of FOAF and WebID forms a decentralised authorization service. WebID is therefore superior to other identity technologies in this way because WebID employs user profile documents as its essential building block and the vocabulary of this building block is FOAF.
- Certificate Authority (CA)
- Certificate authority, or certification authority, (CA) is an entity that issues digital certificates such as those used by HTTPS to secure transactions and to guarantee identity of servers and in some cases clients.
- Further Reading
A. Acknowledgements
Thanks to Tim Berners-Lee for inventing HTML, without which none of this would exist.
The editors would like to thank Shoko Okuma for her contributions to this note.